Can you 3d print a key
This App Lets Anyone 3-D Print 'Do-Not-Duplicate' Keys
In an era when digital tools allow anyone to make practically anything, inscribing the words "do not duplicate" on a key only invites ambitious lock pickers to do exactly that. Now one group of researchers has released a piece of software that makes copying purportedly uncopyable keys easier than ever.
On Tuesday, a group of University of Michigan researchers released a new web-based tool that lets users 3-D print any of thousands of "restricted" keys designed to defy copying attempts. Aside from the "do not duplicate" warnings on restricted keys, lock makers also try to prevent their duplication by using contorted keyways—the space inside a lock that a key's inserted into—and selling the blanks that fit them only to users who can prove their affiliation with a big client like a corporation, university, or government agency.
But the researchers' tool, which they've called Keysforge, is meant to demonstrate that those obscure key shapes no longer offer the security they did before accessible 3-D printing. With little more than the restricted key and a photo of the front of the lock, Keysforge can produce a CAD file ready to 3-D print a working key on any consumer-grade 3-D printer. "We've proven that restricted keyways are no longer a defense," says Michigan researcher Ben Burgess. "We’ve shown that anyone with a 3-D printer can quickly and easily attack these systems."
A 3-D printed copy of a restricted key. University of Michigan
The Michigan researchers aren't quite the first to make that point. In 2013, a pair of MIT students released a piece of software that could copy restricted Primus keys from the lockmaker Schlage. Then a year ago, lock-pickers Jos Weyers and Christian Holler demonstrated to WIRED that they could use a photo of a lock and a quick measurement of its depth to create a 3-D printed "bump" key—a key-shaped tool designed to open a lock by knocking its pins upward when the tool is rapped with a hammer.
But unlike those earlier demonstrations of how 3-D printing can defeat physical security measures, the Michigan researchers' technique works on a wide array of lock systems that use the common A-2 standard of pin spacing inside a lock. Input the series of depth cuts that represent the key's vertical contours—they can be found with a pair of calipers and a chart like this one—and a front-facing photo of the lock it fits into, and the software can automatically generate a CAD file for a duplicate key. And unlike the Photobump creators, the Michigan researchers have also released their software to the public in a bid to definitively demonstrate that restricted keys can be easily copied.
Input the series of depth cuts that represent the key's vertical contours—they can be found with a pair of calipers and a chart like this one—and a front-facing photo of the lock it fits into, and the software can automatically generate a CAD file for a duplicate key. And unlike the Photobump creators, the Michigan researchers have also released their software to the public in a bid to definitively demonstrate that restricted keys can be easily copied.
Replicating restricted keys allows for more than the unlimited copying of a key by, say, a rogue employee: It could also make it possible to duplicate a high-security key from a photograph taken from a distance with a high-powered lens. Researchers showed in 2009 they could find the measurements of a key's cuts from a photograph taken from as far as 200 feet away and at an angle. Like the earlier, unreleased Photobump software, the publicly accessible Keysforge software could enable the easy creation of bump keys for restricted key profiles. Or it could even allow what the researchers call "privilege escalation" attacks, like what University of Pennsylvania computer scientist Matt Blaze has demonstrated. Blazed showed that in a building or facility that uses master keys, a key holder can create a series of keys with small variations on his or her regular key and eventually create a master key that opens many more doors. Using Keysforge to build a series of 3-D printed keys would make that trial-and-error process vastly easier. "One of the biggest defenses for these methods was restricted keyways," says Burgess. "This reopens those attacks."
Or it could even allow what the researchers call "privilege escalation" attacks, like what University of Pennsylvania computer scientist Matt Blaze has demonstrated. Blazed showed that in a building or facility that uses master keys, a key holder can create a series of keys with small variations on his or her regular key and eventually create a master key that opens many more doors. Using Keysforge to build a series of 3-D printed keys would make that trial-and-error process vastly easier. "One of the biggest defenses for these methods was restricted keyways," says Burgess. "This reopens those attacks."
In addition to their proof-of-concept software, the researchers also tried to assess which 3-D printable materials work best for duplicating keys. They tested a variety of printable plastics, and found that the cheap polylactic acid (PLA) plastic used by the popular Makerbot line of 3-D printers was actually stronger than more expensive printers' materials like acrylic and nylon. They found that stainless steel, which can be printed with mail-order services like Shapeways and iMaterialise, was strongest of all, but due to its hardness can damage the internals of a lock. The researchers instead recommend softer brass, which is also available from those commercial printing services. They plan to present all of their research at the Usenix Workshop on Offensive Technologies next week.
The researchers instead recommend softer brass, which is also available from those commercial printing services. They plan to present all of their research at the Usenix Workshop on Offensive Technologies next week.
WIRED reached out to some of the lock companies whose restricted keys could be duplicated with Keysforge, including Medeco, Yale, Schlage, EVVA and BEST. Schlage responded, saying it wasn't ready to comment before publication.
A Medeco spokesperson Clyde Roberson called the Michigan researchers' work "important and informative." He added that the company has been working to create locks with electronic and mechanical components that can't be 3-D printed. "Medeco and [its parent company] ASSA ABLOY have been researching this topic and have been actively pursuing improvements in our technology to help minimize this threat," Roberson wrote in an email. "This includes testing various scanning and printing devices available on the market, from highest quality to lowest. We have already developed some products directly as a result of this work and future products will continue to reflect added protection for this threat."1
We have already developed some products directly as a result of this work and future products will continue to reflect added protection for this threat."1
3D Printed Keys | Hackaday
September 24, 2019 by Tom Nardi
The ability to duplicate keys with a 3D printer is certainly nothing new, but so far we’ve only seen the technique used against relatively low hanging fruit. It’s one thing to print a key that will open a $15 Kwikset deadbolt from the hardware store or a TSA-approved “lock” that’s little more than a toy, but a high-security key is another story. The geometry of these keys is far more complex, making them too challenging to duplicate on a consumer-level printer. Or at least, you’d think so.
Inspired by previous printed keys, [Tiernan] wanted to see if the techniques could be refined for use against high security Abloy Protec locks, which are noted for their resistance to traditional physical attacks such as picking. The resulting STLs are, unsurprisingly, beyond the capabilities of your average desktop FDM printer. But with a sub-$300 USD Anycubic Photon DLP printer, it’s now possible to circumvent these highly regarded locks non-destructively.
The resulting STLs are, unsurprisingly, beyond the capabilities of your average desktop FDM printer. But with a sub-$300 USD Anycubic Photon DLP printer, it’s now possible to circumvent these highly regarded locks non-destructively.
Of course, these keys are far too intricate to duplicate from a single picture, so you’ll need to have the physical key in hand and decode it manually. [Tiernan] wisely leaves that step of the process out, so anyone looking to use this project will need to have a good working knowledge of the Abloy Protec system. Hopefully this keeps bad actors from doing anything too nefarious with this research.
Once you have the decoded values for the key you want to duplicate, you just need to provide them to the OpenSCAD library [Tiernan] has developed and print the resulting STL on your sufficiently high-resolution printer. Generally speaking, the parts produced by resin-based printing have a high tensile strength but are very brittle, so perhaps not the kind of thing you want to stick in your expensive Abloy lock. That said, there are some “Tough Resin” formulations available now which produce parts that are at least as strong as those made with thermoplastics. So while the printed keys might not be strong enough for daily use, they’ll certainly work in a pinch.
That said, there are some “Tough Resin” formulations available now which produce parts that are at least as strong as those made with thermoplastics. So while the printed keys might not be strong enough for daily use, they’ll certainly work in a pinch.
September 18, 2015 by George Graves
We have to hand it to the Transportation Security Administration (TSA). They seem to have a perfect track record of screwing up – and that’s not an easy thing to accomplish if you think about it. If it’s not reports of TSA agents stealing valuables or inappropriately groping passengers, there is the fun fact that in all the years since it was created in 2001, the agency hasn’t caught a single person seeking to do harm in the friendly skies. We’re actually okay with that if it means nobody is trying to do anything shady.
The most recent TSA folly seemed to practically fall into the Internet’s lap when a reporter for the The Washington Post published a hi-res picture of the entire set of TSA master keys while writing an article about how the TSA handles your bags after checking them at the counter. Well, the lock picking community when nuts and in a short time had 3D printed versions available and working. You can see it in action in the (twitter) video after the break.
For those that are not familiar with travel in the US, you are not allowed to use just any old lock on your bags. It has to be approved by the TSA – and that means that they have to be able to open it. So the TSA agents have a set of master keys that can open any bag if they need to look inside for some reason. If you put a non-TSA approved lock on the bag, that can make them a little angry, and you risk having your bag delayed or even cut open.
Of course, you can get into just about any suitcase with a ball point pen, so maybe this isn’t a real “security” issue, but it sure isn’t what you want to see from the agency that is supposed to protect you. Who knew that you could make keys from a photograph? We did way back in 2009 and way more in depth this May… maybe the TSA should start reading Hackaday?
Who knew that you could make keys from a photograph? We did way back in 2009 and way more in depth this May… maybe the TSA should start reading Hackaday?
Continue reading “Dear TSA: This Is Why You Shouldn’t Post Pictures Of Your Keys Online” →
Posted in lockpicking hacks, Slider, Transportation HacksTagged 3D printed keys, lockpicking, TSA, TSA master key3D printed keys | Kaspersky Blog
Hackers are different. For some reason, many of them like to hack not only virtual computer systems, but also quite material objects, such as offices and houses. It is logical that such hackers have to work hard with locks and locking systems. Not surprisingly, at specialized conferences like DEFCON or Chaos Communication Congress, competitions are regularly held to see who has the best master key.
At the 32C3 conference in Hamburg, University of Colorado professor Eric Wurstow gave a talk on the use of 3D printers in the difficult task of counterfeiting cylinder lock keys used in most locking systems.
Before the advent of 3D printers, it was not so easy to make a copy of a key: an experienced metal carver or a specialist with experience in setting up and programming specialized machines would have coped with such a task. In addition to qualified personnel, a burglar would need a suitable blank and, most importantly, the original or at least a cast of the key. With the advent of 3D scanning and printing technology, copies have become much easier and even cheaper.
There are at least three ways to use 3D technology to make a fake.
First, it's enough to take a picture of the original key with a high-resolution camera and turn the picture into a 3D model. It is enough to print a valid copy. In addition, modern telephoto lenses are so good that you can really take a suitable picture from afar.
The second method is called bumping. The burglar prints a special bumping key, inserts it into the lock and lightly taps it with a hammer. From the impact, the pins in the lock are thrown up. With due skill, the burglar turns the bumping key at the right moment and opens the lock. 3D printed plastic keys are even better for bumping than regular metal blanks, as the plastic is not as noisy, transfers shock better and reduces the risk of damage to the lock. And, of course, printing a key is easier than filing a metal blank by hand.
The third way is probably the most interesting. It allows you to crack the master key system itself, so Wurstow called it "Privilege Elevation" by analogy with the computer hacking technique of the same name. The master key system is based on the popular practice of producing locks that are compatible with two different keys at the same time. Manufacturers supply locks with two sets of pins - for ordinary keys and for the master key, respectively. Typically, a master key will fit multiple locks in the same business, as they contain the same extra set of pins.
Manufacturers supply locks with two sets of pins - for ordinary keys and for the master key, respectively. Typically, a master key will fit multiple locks in the same business, as they contain the same extra set of pins.
The problem is that not all sets of pins are completely different from each other. If a burglar has a regular key for a similar lock, he can scan it, create a 3D model and print many keys with a modified set of grooves. Sooner or later one of the keys will fit.
So, one by one, a burglar can modify the grooves - and as a result, he will receive a master key that fits all doors. In this case, 3D printing will come in especially handy - this method requires many approaches, and each approach requires a new, modified key.
Of course, not every printer can print a normal key. Depending on the media selected, copies may come out too fragile or too soft. But there are printers that work with materials suitable for this. In addition, if home 3D printers print mostly plastic figures, you can always contact a special service where 3D printers can work with copper, steel, or even titanium alloy.
It is worth noting that the keys printed on a 3D printer are not a theoretical problem at all. It has long been possible to find both key forgery software and 3D printers on the market. The most notorious master key incident was the leak of images containing images of TSA master keys, which the US Transportation Security Administration uses to unlock locks on travel suitcases. The craftsmen made a fuss and quickly published 3D models based on these pictures on the Web, so now anyone can print out the cherished key to your luggage.
REVEALED: TSA has a master key for your luggage and people are making copies @BI_Video http://t.co/P5bod70zUK pic.twitter.com/oZ9jspPXqB
— Business Insider (@businessinsider) September 11, 2015
So how can you protect yourself and your property? From our point of view, it is most obvious to draw a parallel with passwords, which, in fact, are digital analogues of keys. We offer you a few simple rules, which, of course, will not provide you with 100% protection, but it will make access to your apartment so difficult that a burglar will most likely prefer to look for an easier victim.
We offer you a few simple rules, which, of course, will not provide you with 100% protection, but it will make access to your apartment so difficult that a burglar will most likely prefer to look for an easier victim.
Very useful topic: how to use passwords - 10 simple rules: https://t.co/RtQTf2Mm7T pic.twitter.com/XP6vrwJShJ
— Kaspersky Lab (@Kaspersky_ru) December 21, 2015
1. Do not use "simple" keys, just like simple passwords. An ordinary cylinder lock is almost as insecure as the password "123456" and "masha1975". If you are concerned about security, install a comprehensive door lock system.
2. Use an analogue of "two-factor authentication". Two different types of locks will be much more effective than one.
3. Don't compromise your "password", that is, try not to get the keys to the apartment in front of the cameras and, of course, do not publish their photos online. Even a bad photo is enough to create a working 3D model, and with it a copy.
4. The master key is a kind of "backdoor", a loophole to your office. Do not install such locks in rooms where security is important.
5. A professional security solution never hurts: the alarm will protect you from the most persistent burglars and thieves.
Tips
Fake financial regulators
In emails, scammers pretend to be representatives of government agencies in order to swindle users of their personal data and money.
Air sellers in online stores
We tell how scammers deceive users of a well-known marketplace using a fake payment page for goods.
Subscribe to our weekly newsletter
- Email*
- *
- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site. I can withdraw my consent at any time by clicking on the "unsubscribe" button at the end of any of the emails sent to me for the above reasons.

- I agree to provide my email address to AO Kaspersky Lab in order to receive notifications of new publications on the site. I can withdraw my consent at any time by clicking on the "unsubscribe" button at the end of any of the emails sent to me for the above reasons.
A 3D printer can print an exact copy of a high-level security key from a photo
By engraving "do not copy" on the keys of high security locks, Schlage locks wanted to create another obstacle for those who would like to make a copy of a key that not everyone can copy anyway. Instead, there were people who took this inscription as a challenge.
At the Def Con hacker conference on Saturday, MIT students David Lawrence and Eric Van Albert plan to unveil code that allows anyone to create a 3D-printable computer model of any Primus key, despite the manufacturer's best efforts to prevent copying specially designed keys. Armed with a conventional scanner and their software, they were able to create accurate computer models of the keys, which they then printed in titanium or nylon on online 3D printing services such as Shapeways and i.Materialize. You can learn more about such services in this video.
Schlage's Primus locks are positioned as locks for use in places where a high level of security is required: Schlage advertised these locks as being used in government offices, healthcare centers and prisons. Part of this high level of security is due to the two lanes, one on the edge of the key and one in the middle. Each of these two tracks has its own set of locking pins in the lock. Mark Weber Tobias, one of the world's most famous lockpicking experts, wrote that he uses Primus locks both at home and at work.
Part of this high level of security is due to the two lanes, one on the edge of the key and one in the middle. Each of these two tracks has its own set of locking pins in the lock. Mark Weber Tobias, one of the world's most famous lockpicking experts, wrote that he uses Primus locks both at home and at work.
Of course, Lawrence and Van Albert's program does not allow you to open any doors locked with one of these locks. It just allows its users to easily copy a key that was previously very difficult to forge. However, the same MIT students insist that it is possible to get a working copy of the key without ever touching the original. It has long been no secret that you can create an exact copy of the key even on the basis of photographs, sometimes even from photographs taken at a distance of many tens of meters. (See, for example, the Sneakey project). By studying user manuals and Schalge patents, Lawrence and Van Albert learned to recognize two codes in the form of keys: a 6-digit code that corresponds to cutouts on the edge of the key, and a 5-digit code encrypted by cutouts on the key plane. Having recognized and put these codes into the program, you can create a copy of the key.
Having recognized and put these codes into the program, you can create a copy of the key.
As Lawrence says:
All you need is a friend who works at the establishment who can take a picture of the key, and it could even be a picture of the key dangling from a key ring on someone's belt. Forgery of keys becomes like pirated distribution of films: someone has to get this information, however, then everyone can use this information.
Although we are talking about Primus locks, Lawrence and Van Albert argue that the same technique can be applied to any high-security lock:
We want to convey to people that this is easy to do with any lock, regardless of its price tag. As for the Primus locks, it didn't take that long. In the future, it will be easy to find models on the Internet for making copies of almost any type of key.
Lawrence and Van Albert refer to a recent story with published photographs of New York's fire elevator keys, which give access to many of New York's electrical panels, elevator control panels, and subway entrances.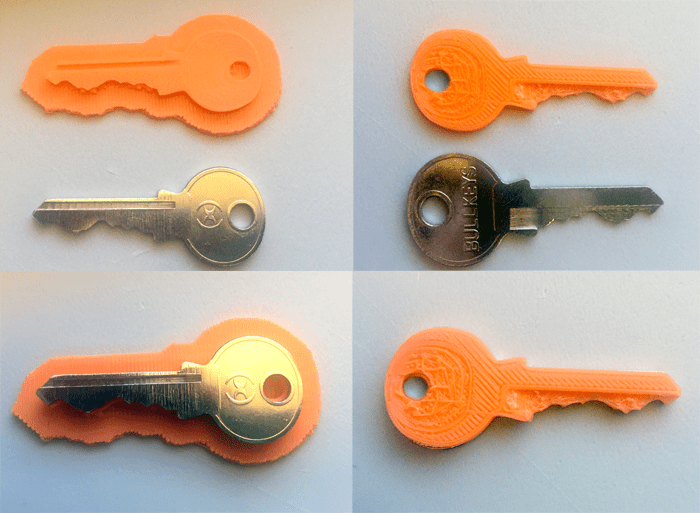 These photos were published in a New York newspaper last fall. It is quite ironic that the newspaper article was written to warn the public that these keys, handed out to the city's electricians and firefighters, could easily fall into the wrong hands, however, a high-resolution photo of the keys themselves made it possible for everyone to print a copy for themselves. these same keys on a 3D printer. The editors quickly realized their mistake, and immediately removed the photo from their website, but it was too late, and the images of the keys managed to spread throughout the network.
These photos were published in a New York newspaper last fall. It is quite ironic that the newspaper article was written to warn the public that these keys, handed out to the city's electricians and firefighters, could easily fall into the wrong hands, however, a high-resolution photo of the keys themselves made it possible for everyone to print a copy for themselves. these same keys on a 3D printer. The editors quickly realized their mistake, and immediately removed the photo from their website, but it was too late, and the images of the keys managed to spread throughout the network.
I must say that this is not the first case of printing a copy of the key on a 3D printer. In 2011, an Apple engineer wrote a program that allows, based on key measurements, to create a three-dimensional model suitable for printing on 3D printers. True, then it was about ordinary keys, which are not difficult to make in any of the many special shops.
Last year, at the HOPE hacker conference, a hacker known as "Ray" showed that he could 3D print a working copy of the keys to highly secure handcuffs. Usually access to handcuff keys is limited, but they are all identical so that one policeman can remove the handcuffs fastened by another policeman, which makes this system quite vulnerable, because now it is possible to make a copy of these small keys for yourself, and hide it on your body, so that you can free yourself if necessary.
Usually access to handcuff keys is limited, but they are all identical so that one policeman can remove the handcuffs fastened by another policeman, which makes this system quite vulnerable, because now it is possible to make a copy of these small keys for yourself, and hide it on your body, so that you can free yourself if necessary.
As for the problem with the Schlage keys, Lawrence and Van Albert have no easy solution. They believe that in the age of 3D printing, the concept of high-security mechanical locks will be outdated. Instead of mechanical locks in places where a high level of security is required, electronic locks with unique cryptographic keys, which are harder to counterfeit, should be used.
We hope that if we show the world that any mechanical lock can be bypassed by simply downloading a few numbers from the Internet, the transition to stronger security methods will happen faster, says Van Albert.
We recently published an article that when the patents for laser sintering technology expire in 2013, there will be cheap consumer 3D printers using this technology.